What Is A Checksum Ck3 A checksum simply verifies with a high degree of confidence that there was no corruption causing a copied file to differ from the original for varying definitions of high In
You are correctly though that if a machine is doing all the work you probably don t need to have both a checksum and a signature as the signature will perform the checksum for The file s fingerprint checksum is there to tell you that the file is not altered An attacker may host a malicious version of PuTTY on his website and makes it available to
What Is A Checksum Ck3

What Is A Checksum Ck3
https://i.ytimg.com/vi/ChV1e_aOgNY/maxresdefault.jpg

What Is Checksum Error Detection What Is Checksum And How It Works
https://i.ytimg.com/vi/Ig8t6MhroB8/maxresdefault.jpg
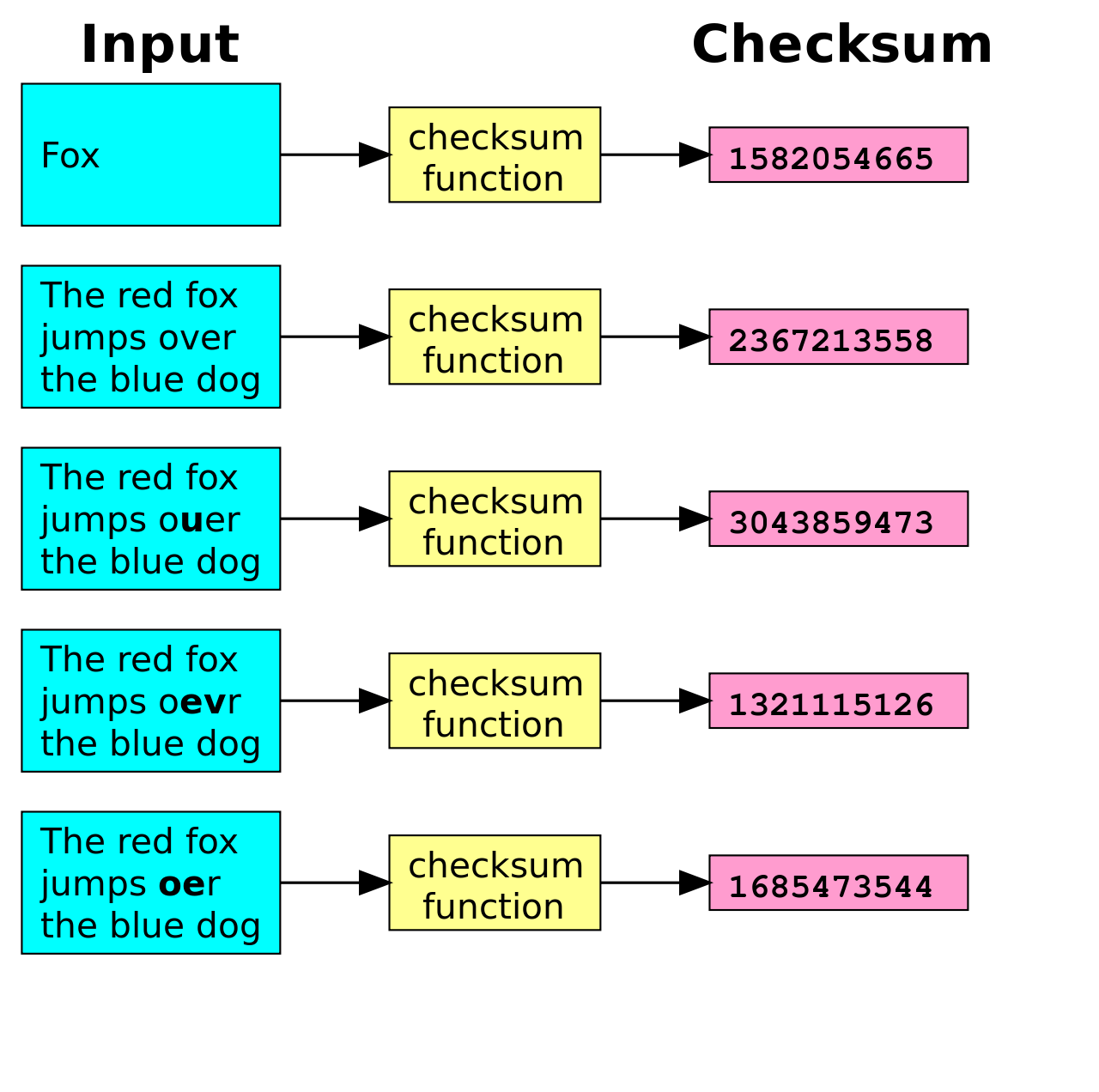
Checksum
https://velog.velcdn.com/images/asap0208/post/9c511980-dada-46e7-b0cc-f97143bcc6da/image.png
Checksum solves the problem of integrity you know that what you just downloaded is correct but you do not know from who it comes If someone is operating a MitM IP checksum IP 20 ICMP checksum 2
If the organization hosting the downloadable file simply posts the checksum of the file along with the file then you are right If an attacker manages to breach the server and Since the signature is included in the file it will change the checksum if you pass it through a regular hashing program like MD5SUM File Signing is format specific i e the way
More picture related to What Is A Checksum Ck3
Checksum
http://www.myreadingroom.co.in/images/stories/docs/dcn/checksum.JPG
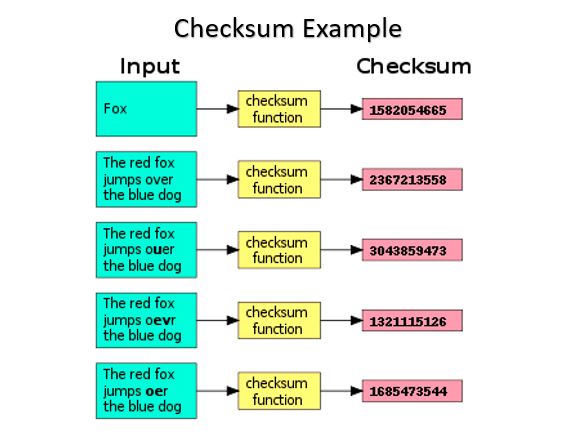
Checksum
https://www.how2shout.com/wp-content/uploads/2019/03/What-are-checksums-How-to-find-the-checksum-of-a-file-All-you-need-to-know.jpg
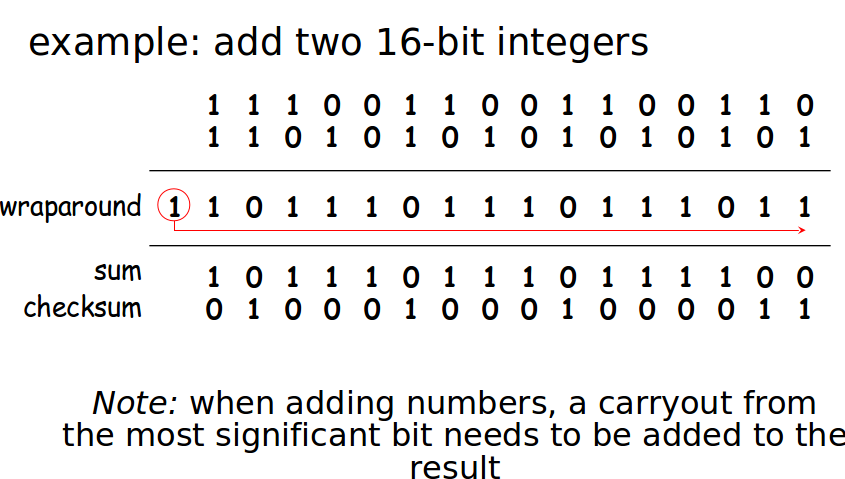
Checksum
https://you.stonybrook.edu/ylatif/files/2016/04/internet-checksum-example-2a544mv.png
The MD5 checksum is about downloading the big archive through HTTP possibly from a mirror while obtaining the MD5 value from a secure Web site HTTPS This way you just need to Not everyone might download via HTTPS The practice of releasing a checksum together with a file predates the widespread use of HTTPS Furthermore the storage media
[desc-10] [desc-11]
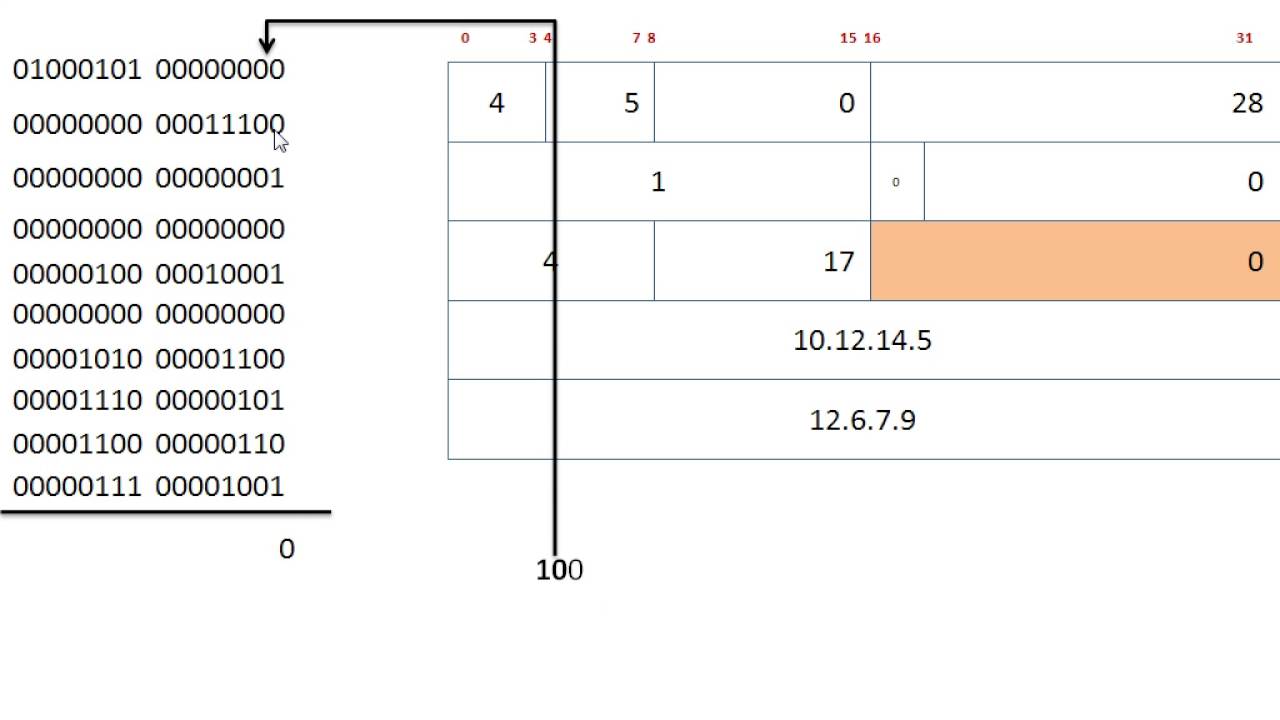
Checksum
https://i.ytimg.com/vi/dXartoyj2ow/maxresdefault.jpg

Checksum Algorithm Ploraright
https://i.ytimg.com/vi/WOXO7z05ATM/maxresdefault.jpg

https://security.stackexchange.com › questions
A checksum simply verifies with a high degree of confidence that there was no corruption causing a copied file to differ from the original for varying definitions of high In

https://security.stackexchange.com › questions
You are correctly though that if a machine is doing all the work you probably don t need to have both a checksum and a signature as the signature will perform the checksum for
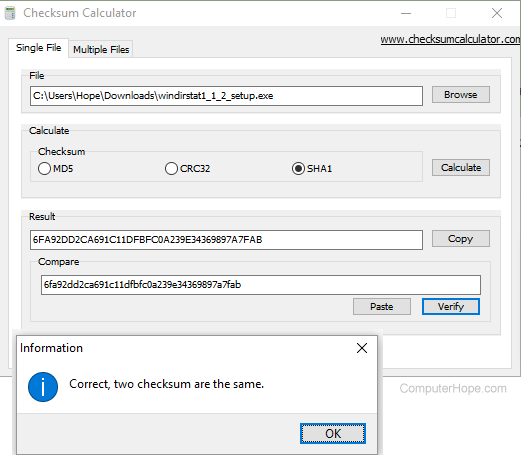
Fciv Tool

Checksum

Checksum Diagram
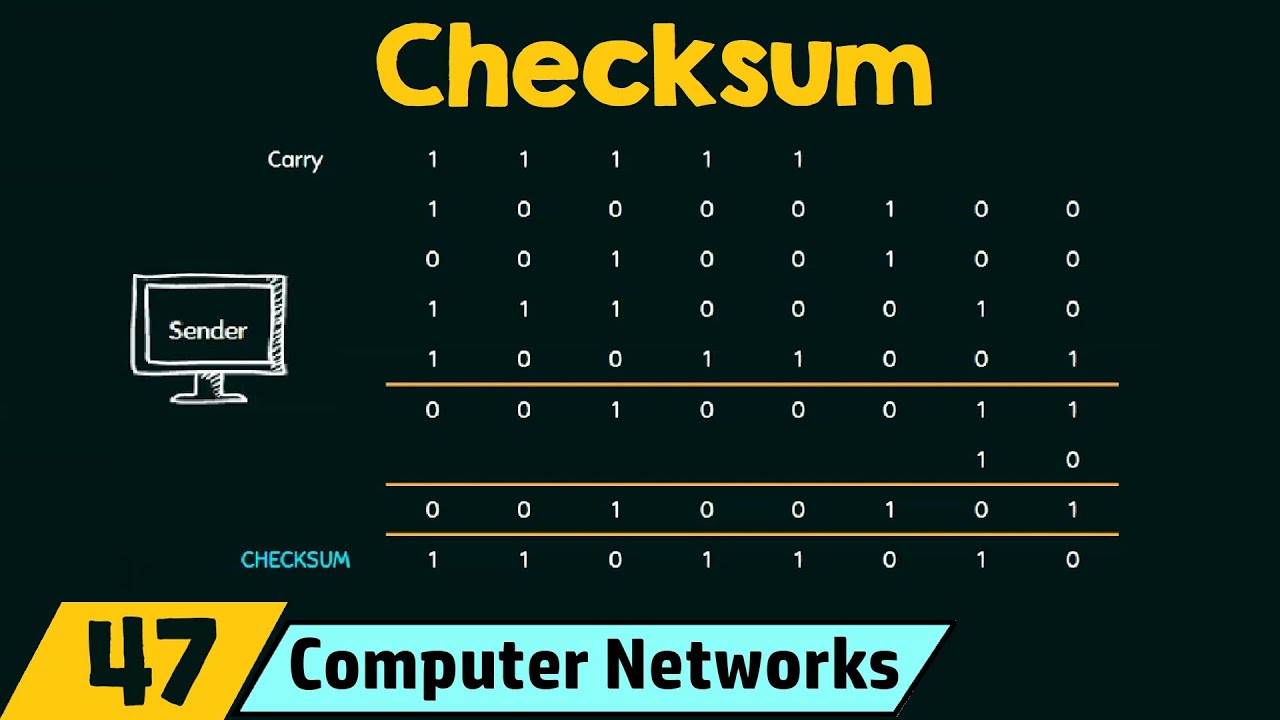
Checksum Diagram
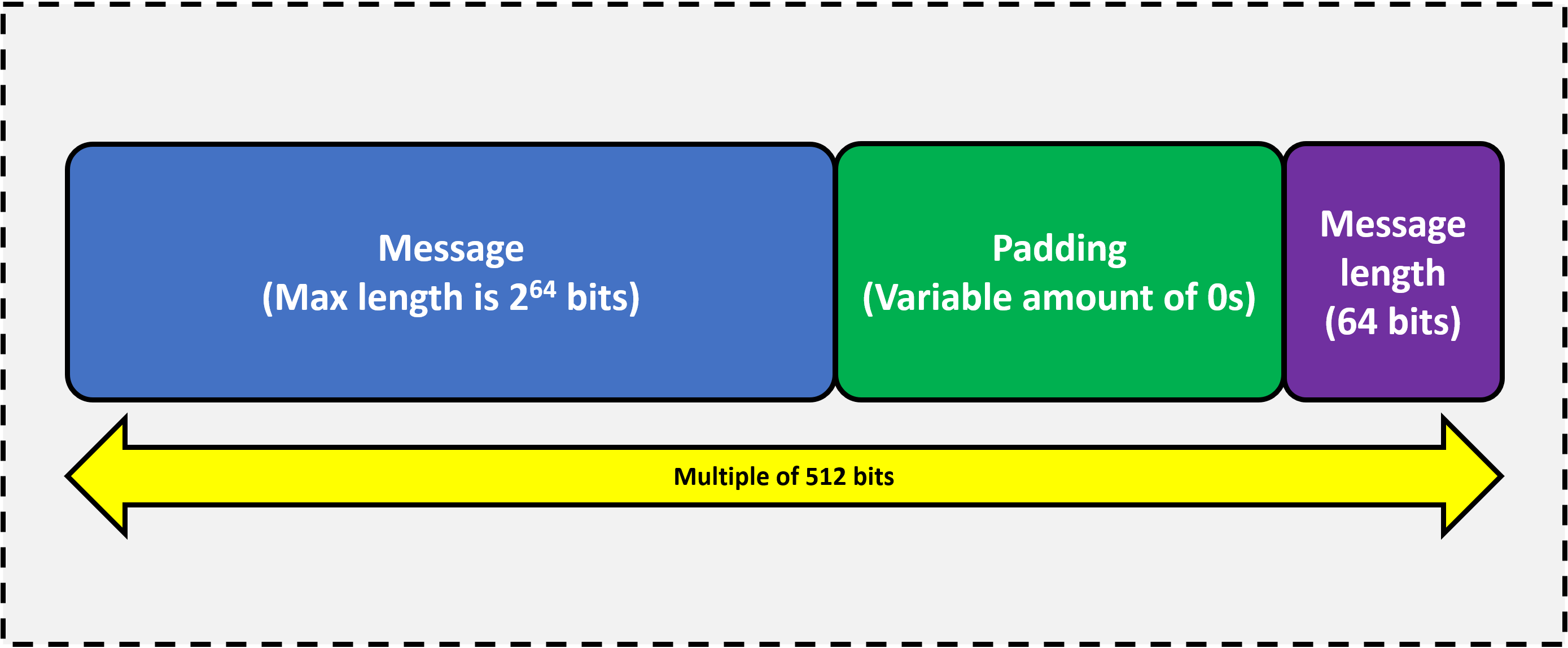
Checksum Diagram
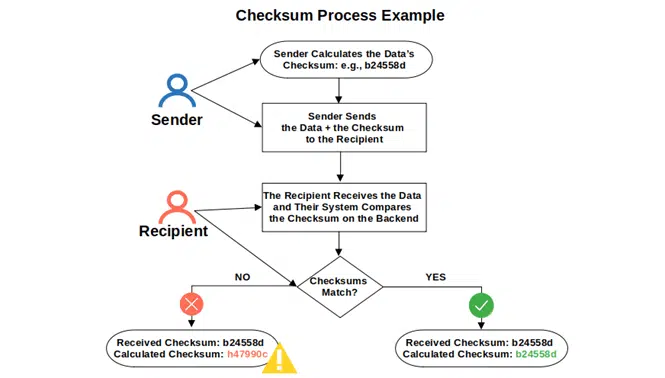
Checksum Diagram

Checksum Diagram
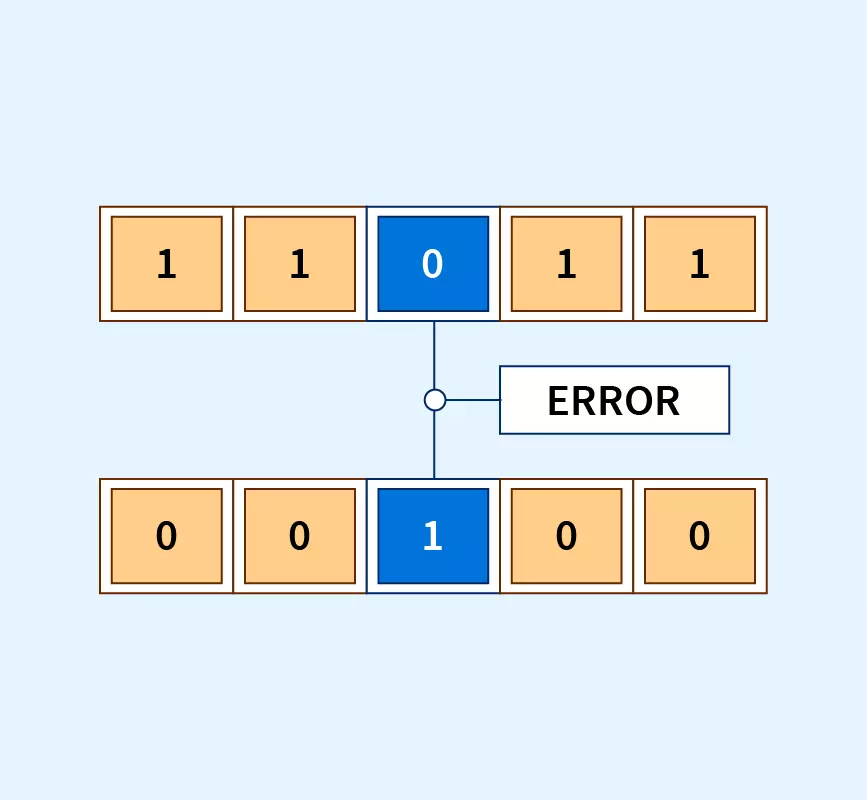
Checksum Diagram
CK3 Concubines How They Work How To Get Them FandomSpot
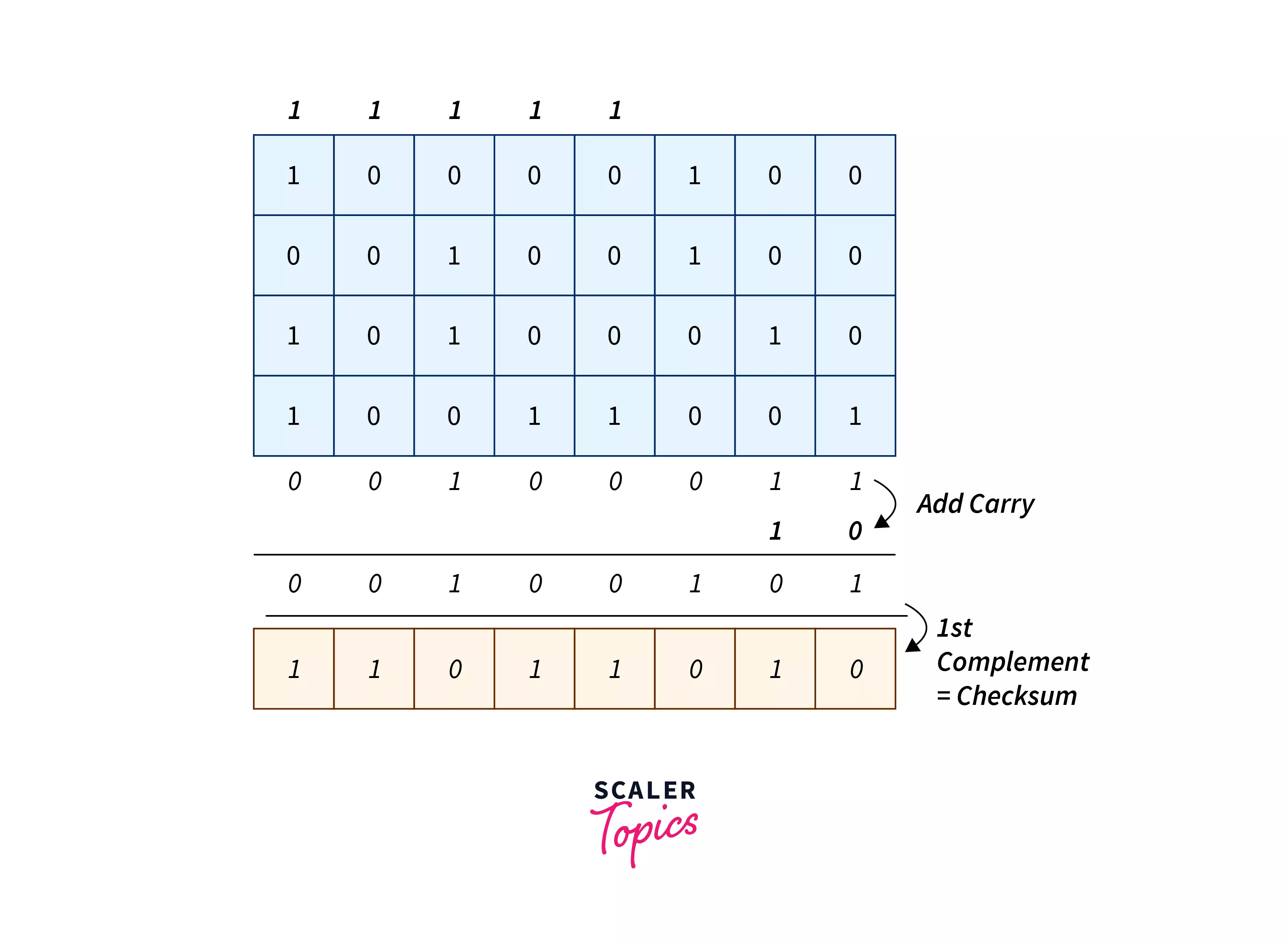
What Is Checksum Scaler Topics
What Is A Checksum Ck3 - If the organization hosting the downloadable file simply posts the checksum of the file along with the file then you are right If an attacker manages to breach the server and
