What Is A Checksum Used For IP checksum IP 20 ICMP checksum 2
You are correctly though that if a machine is doing all the work you probably don t need to have both a checksum and a signature as the signature will perform the checksum for A checksum simply verifies with a high degree of confidence that there was no corruption causing a copied file to differ from the original for varying definitions of high In
What Is A Checksum Used For

What Is A Checksum Used For
https://i.ytimg.com/vi/JxTUZdTf09E/maxresdefault.jpg
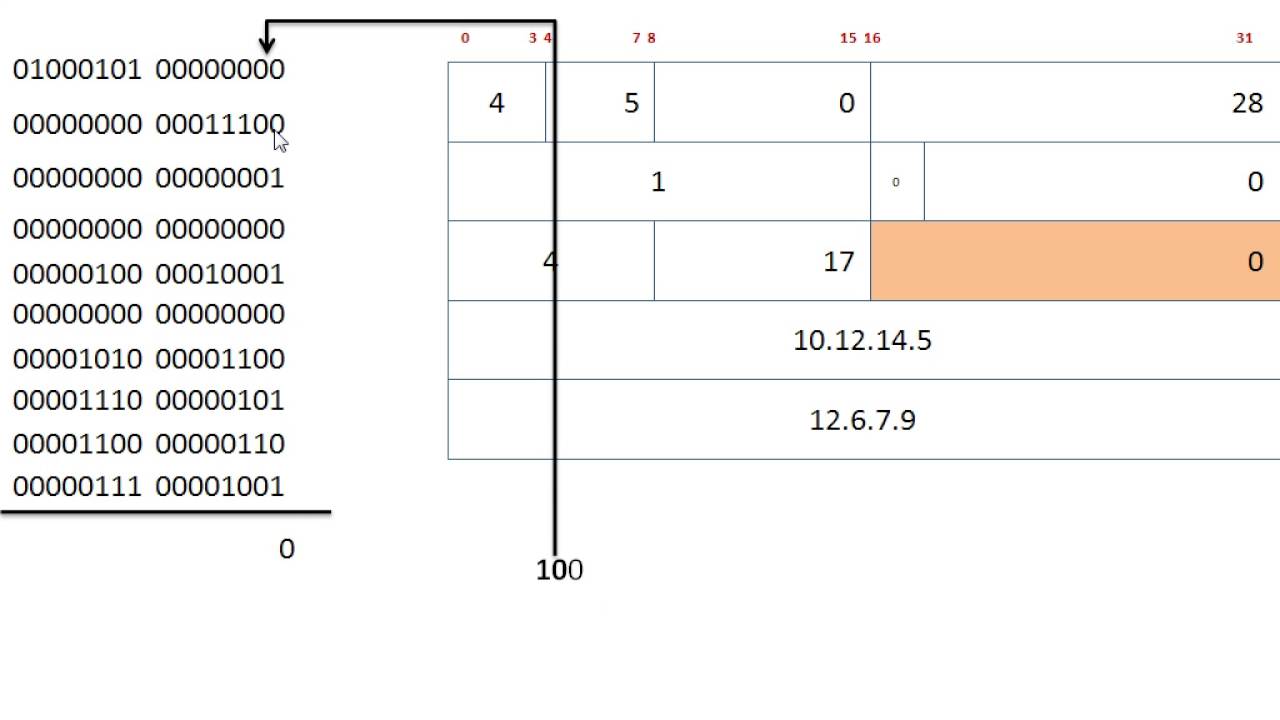
How Checksum Is Calculated In IP Packets At Network Layer YouTube
https://i.ytimg.com/vi/dXartoyj2ow/maxresdefault.jpg

What Is Checksum And How To Calculate Checksums YouTube
https://i.ytimg.com/vi/ChV1e_aOgNY/maxresdefault.jpg
CRC Checksum CAN Msg ETH PDU Checksum Checksum CRC The file s fingerprint checksum is there to tell you that the file is not altered An attacker may host a malicious version of PuTTY on his website and makes it available to
Checksum solves the problem of integrity you know that what you just downloaded is correct but you do not know from who it comes If someone is operating a MitM Checksum CRC 8bit CAN CRC CAN CAN
More picture related to What Is A Checksum Used For

Checksums The Luhn Algorithm For Verifying Credit Card Numbers YouTube
https://i.ytimg.com/vi/kMpEj7roKxM/maxresdefault.jpg?sqp=-oaymwEmCIAKENAF8quKqQMa8AEB-AH-CYAC0AWKAgwIABABGGUgYihTMA8=&rs=AOn4CLBjTVLuyVIfJ3pJ2uSlMhRialC9gg

What Is Checksum Error Detection What Is Checksum And How It Works
https://i.ytimg.com/vi/Ig8t6MhroB8/maxresdefault.jpg

Checksum In Computer Networks Error Detection Technique Part 4
https://i.ytimg.com/vi/aJDjjfwHcLs/maxresdefault.jpg
cmos checksum error defaults loaded CMOS BIOS 4 1 Since the signature is included in the file it will change the checksum if you pass it through a regular hashing program like MD5SUM File Signing is format specific i e the way
[desc-10] [desc-11]

Checksum In Computer Networks CHECKSUM Error Detection Technique
https://i.ytimg.com/vi/CxjrrWt9CLU/maxresdefault.jpg
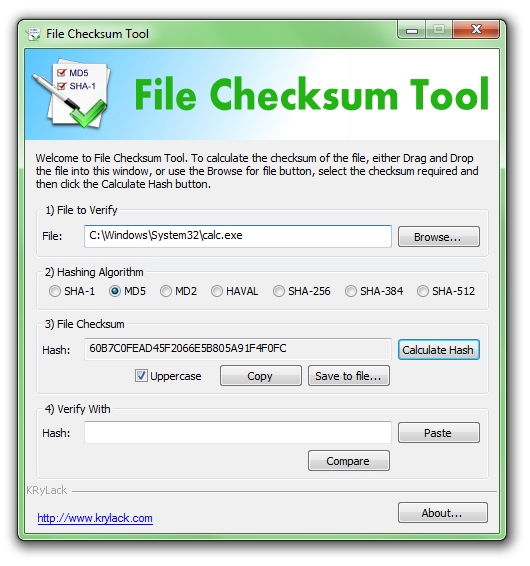
File Checksum Tool KRyLack Software
https://www.krylack.com/images/file-checksum-tool-screenshot.jpg


https://security.stackexchange.com › questions
You are correctly though that if a machine is doing all the work you probably don t need to have both a checksum and a signature as the signature will perform the checksum for

Checksum

Checksum In Computer Networks CHECKSUM Error Detection Technique
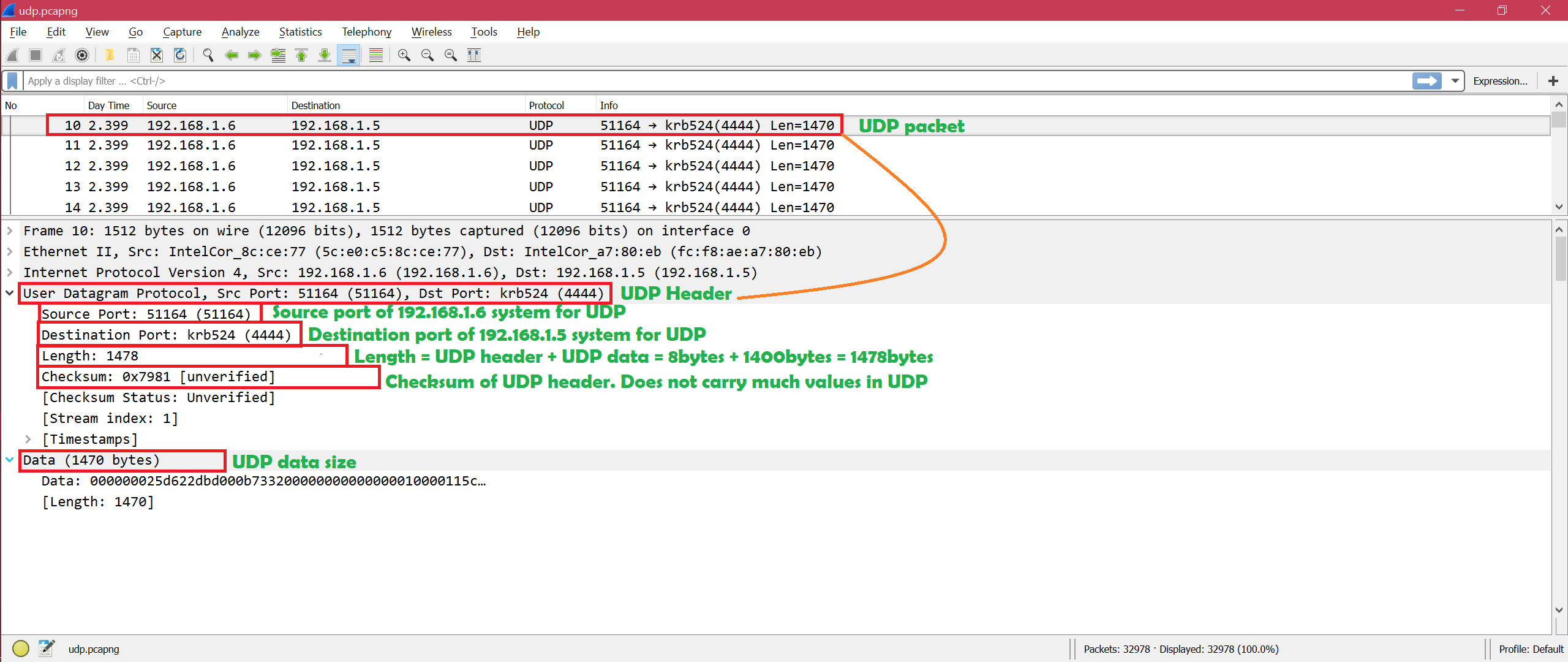
UDP Wireshark Analysis
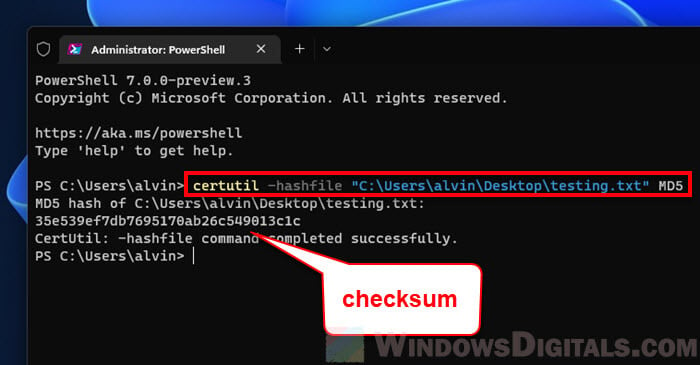
Certutil Sha256

What Is MD5 Checksum And How To Use It YouTube

Checksum Diagram

Checksum Diagram
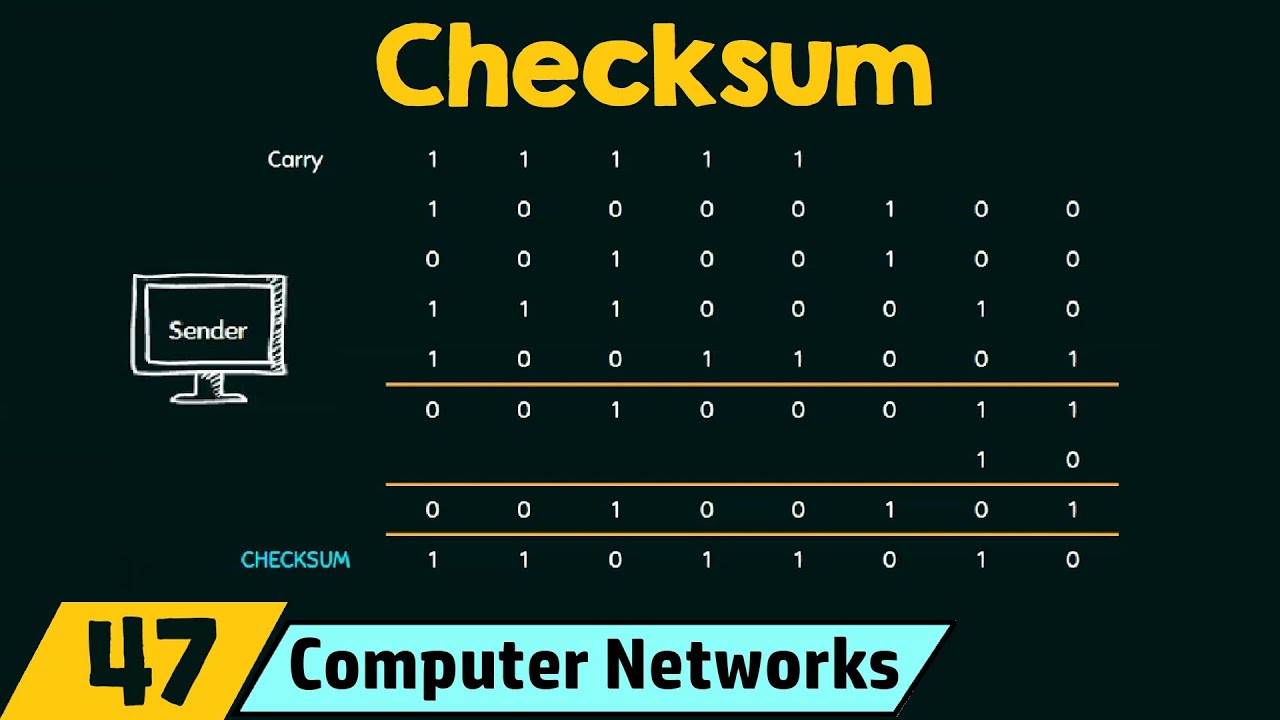
Checksum Diagram
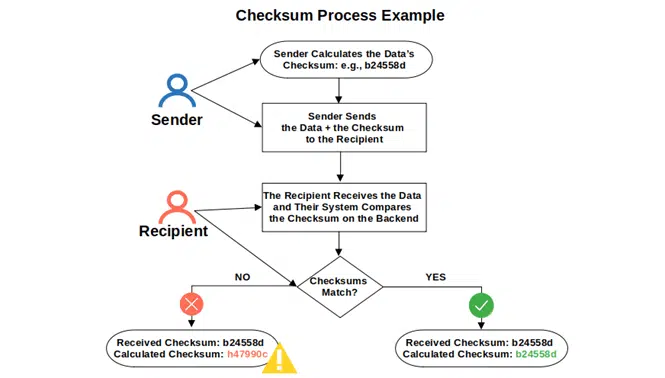
Checksum Diagram
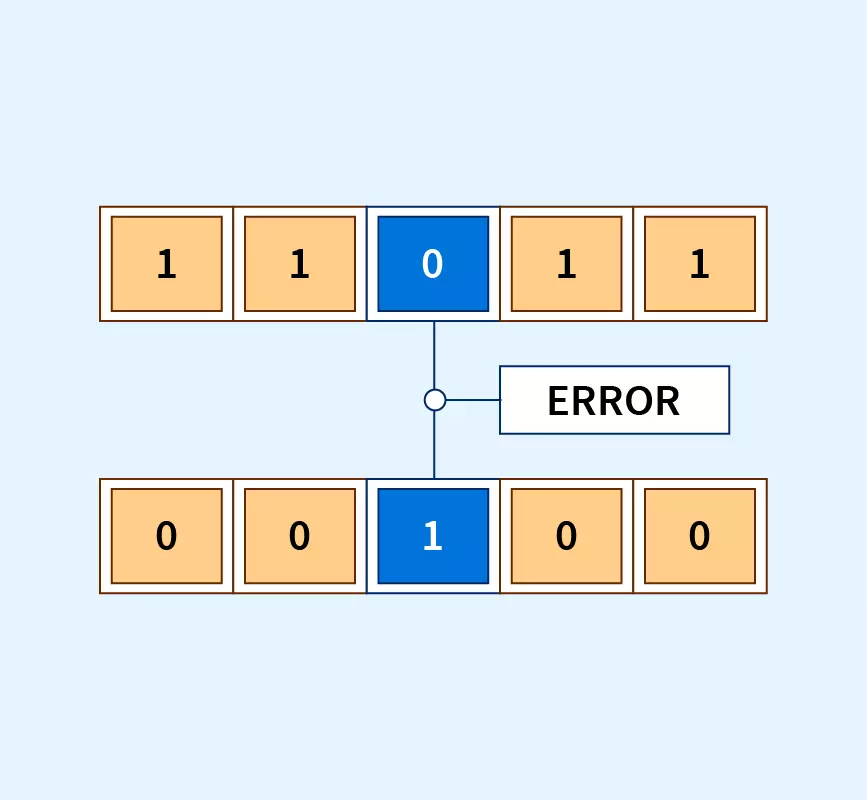
Checksum Diagram
What Is A Checksum Used For - Checksum solves the problem of integrity you know that what you just downloaded is correct but you do not know from who it comes If someone is operating a MitM